💻Our Ethical Hacking Resources💻
Here you will find information about the **hack tools** we develop and use. We specialize in testing security vulnerabilities to make systems more robust (ethical hacking).
💻Safety First💻
All our tools are intended for legal and ethical purposes, such als penetration testing and security audits, with the explicit permission of the system owner.
🖥️List of Hacktools: Linux-Kali -Android
1. Spyware Software
2. DDoS-Attack Software
3. SQL-Map Software
4. Phishing Software
5. Pentest Software
6. Metasploit Framework Software
7. Sniffing and Spoofing Software
8. Network Scanner Software
9. Password Attacks Software
10. SQL-Injection Software
11. People Hunt Software
12. API Scanner
13. Wordpress scanner
14. IP location tracker software
15. Stresstest Software
16. Forensics Tools Software
17. Information Gathering Software
18. Web Hacking Software
19. Vulnerability Scanner Software
20. Web Servers Software
21. Nmap Software
---------------------
Send an Email to order the Hacking software. You will then receive an invoice from us. After payment, the software will be emailed to you.
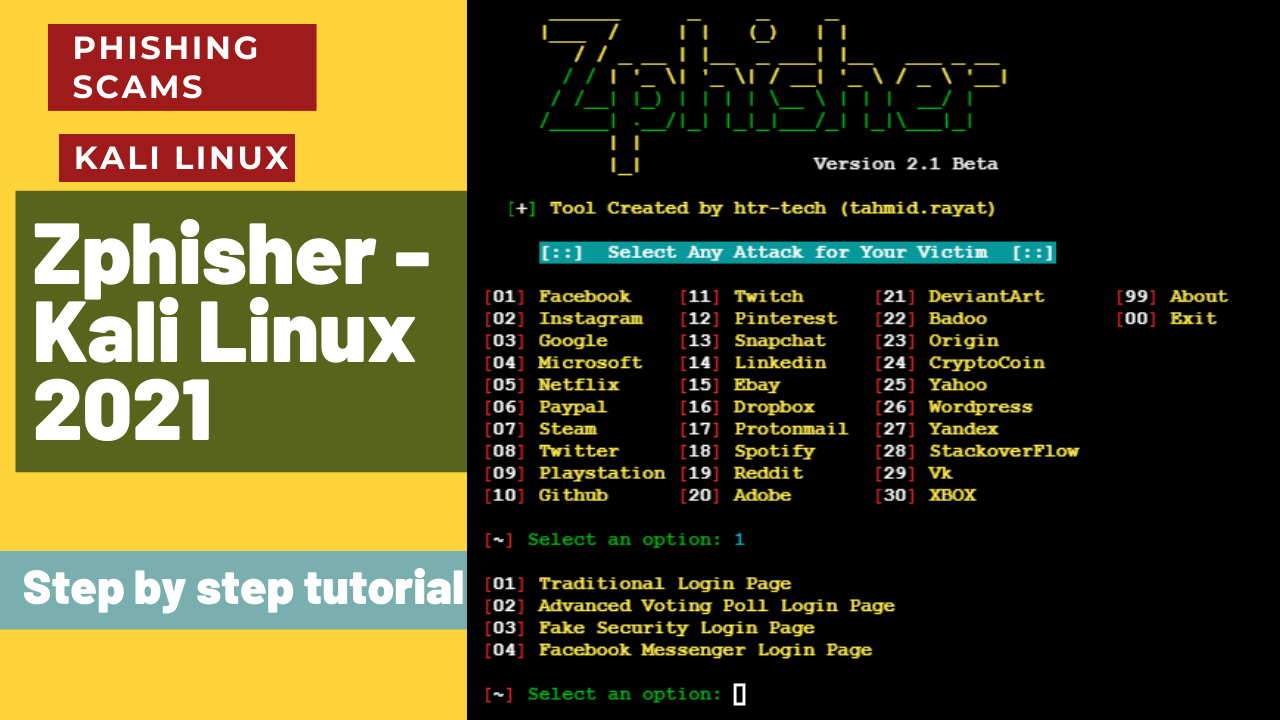
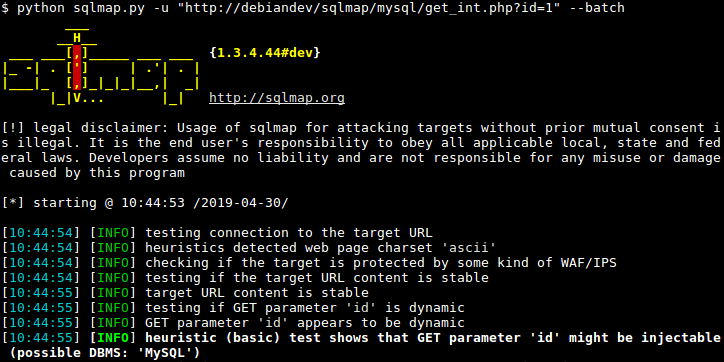
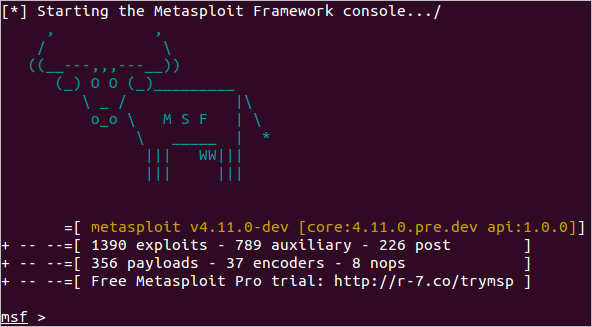
🖥️Extra Information about our Hacktools 🖥️
1. Network and Vulnerability Mapping
These tools are crucial for discovering network topology and identifying weak points.
- **Nmap (Network Mapper):** An open-source utility for network discovery and security auditing. It can detect hosts, services, operating systems, and open ports on a network.
- **Wireshark:** The world's foremost network protocol analyzer. It allows you to interactively browse and inspect data packets captured from a live network or from a file.
- **Nessus:** A popular vulnerability scanner (available in free/paid versions) that performs comprehensive checks for configuration weaknesses and missing patches.
- **Nikto:** A simple but powerful open-source web server scanner that checks for dangerous files/CGIs, outdated server software, and other configuration issues.
2. Web Application Security and Proxies
Essential tools for testing the security of modern web applications.
- **Burp Suite (Community/Professional):** An integrated platform of tools used for performing security testing of web applications. It acts as a proxy to intercept, inspect, and modify traffic between the browser and the web server.
- **OWASP ZAP (Zed Attack Proxy):** A free, open-source security tool maintained by the international OWASP community, used for finding vulnerabilities in web applications.
3. Password Cracking and Authentication
Tools for testing the strength of authentication mechanisms and credentials.
- **John the Ripper (JtR):** A fast password cracker that is commonly used to detect weak Unix passwords, but supports many hash and cipher types.
- **Hashcat:** Touted as the world's fastest and most advanced password recovery tool, supporting five unique modes of attack and a massive number of hash types.
- **Hydra:** A powerful, fast network logon cracker that supports numerous protocols to attack login services such as SSH, FTP, Telnet, and more.
4. Wireless Network Auditing
Specific tools for assessing the security of Wi-Fi networks.
- **Aircrack-ng Suite:** A complete set of tools for assessing WiFi network security. It focuses on monitoring, attacking, testing, and cracking wireless connections.